
Hi everyone im the GrayHatter and thats my Blog.
Cibersecurity and IoT passioner and system administrator in Cesur Formación especialiced in cibersecurity and linux administración
In the daily activities of a Pentester or Ethical Hacker is necesary to use a long variety of tools to do the penetration test more efficient and fast. From the first footprinting scanning to the last privilege elevation script, pentesters have access to lots of tools writer by community Partners.
One of the principal vectors to gain access to a machine is the 80/tcp port that in general is served by the http protocol but obviously that requieres port scanning first. When you are enumerating that port, in specifically the http server directories (dir indexing) the comminity doesnt private us to have a great variety of that kind of tools such dirbuster, dirb or Dirsearch that is the last one that im going to talk about.
Indexing http servers is one of the most important step to follow to direct your test to the good way.
Dirsearch is writed in python3, is a powerfull tool that bring us the posibility to index and fuzz urls in the http server sending requests to it and waiting for a http response like 200,500,etc.
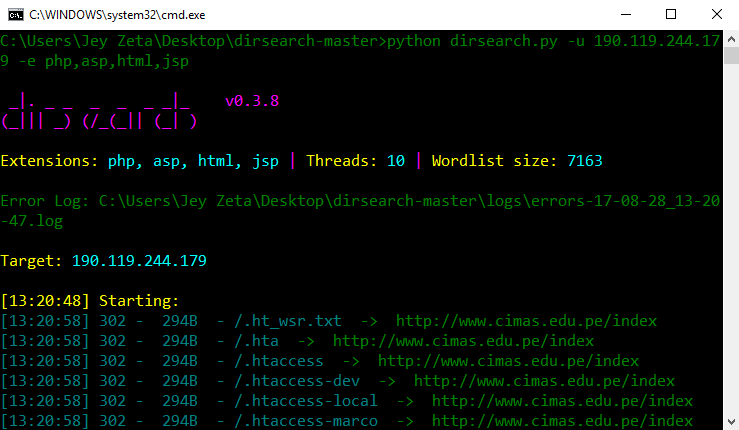
You can know more about dirsearch proyect in:
https://github.com/maurosoria/dirsearch
In my experience using this tool i can say that is really fast and powerfull but one negative point is that if you miss one relevant parameter such -x that ingnores certains http responsers, the server can response to every request with code 500 so dirsearch work can converse into a eternity and not oriented your pentest properly.

Another relevant parameter is the -r parameter that search directories recursively into the accepted urls so dirsearch will restart a new search into every new descovered directory.
We cannot forget about the -f option. Pruebe and error is a very effective method to learn. Time ago doing a dir indexing over a http i had to search for a certain .txt file and i setted up with -e txt. Since here good, but at the momment that i started to launch diccs, nothing clair was in the output. Looking in -h i looked for something helpfull and it was the -f parameter that allow to force the extension, like in dirbuster and that was great because then i could recuperate the hidde .txt with a very common dicc. That is a probe that the -f parameter needs to be used in most of the cases especifically in the recursive searching.
I highly recommended practice a understand the options and parameters and use the common sense in the indexing task.
The conclusion is that dirsearch can greatly help you if you have a light idea of what are you looking for atrending to the server response, clues about tipes of extension (for example an aspnet api of a widows server) and no discarting do the recursive searching. Then you can play with the headers, threads, list of extensions and more other parameters and combinations that i invited you to look and investigate. If not it can converse into the first rabbit hole that youre going to find in your pentesting.
Another important point related to it is use the correct wordlist. Dirsearch has one by default.

But that is other post


Deja un comentario